Last month, a creator I’ve followed for years lost everything. Not gradually—overnight. Someone hacked her Instagram account with 180,000 followers, changed the password, locked her out, and started running crypto scams on her audience. By the time Instagram restored her account three weeks later, she’d lost 40% of her followers and her reputation was in shambles.
The scariest part? She thought she was being careful.
Social media security isn’t sexy. It doesn’t get likes or drive engagement. Most people ignore it completely until disaster strikes. Then it’s too late. You’re locked out of your account, watching someone else control your brand, contact your followers, access your business data.

When republishing content, confirm rights first—then use this tutorial to remove watermark from video with AI the responsible way.
I’m not here to scare you, but I am here to wake you up. Growing your social media presence means nothing if you can’t protect what you build. Let’s fix that.
Table of Contents
Understanding the Real Threats
Phishing attacks remain the number one way accounts get compromised. You receive a DM: “Hi! We want to verify your account. Click here.” The link looks legitimate. You click, enter your password, and someone now owns your account.
Weak passwords are another massive vulnerability. “Instagram123” isn’t protecting anything. Hackers use automated tools trying thousands of common combinations per second.
Third-party apps create security holes. Every app connected to your accounts has some level of access. When these services get hacked, your accounts become vulnerable.
SIM swapping is increasingly common. Hackers contact your carrier, impersonate you, and transfer your number to their device. They receive your 2FA codes, reset your passwords, and own your accounts.
The Foundation: Password Security
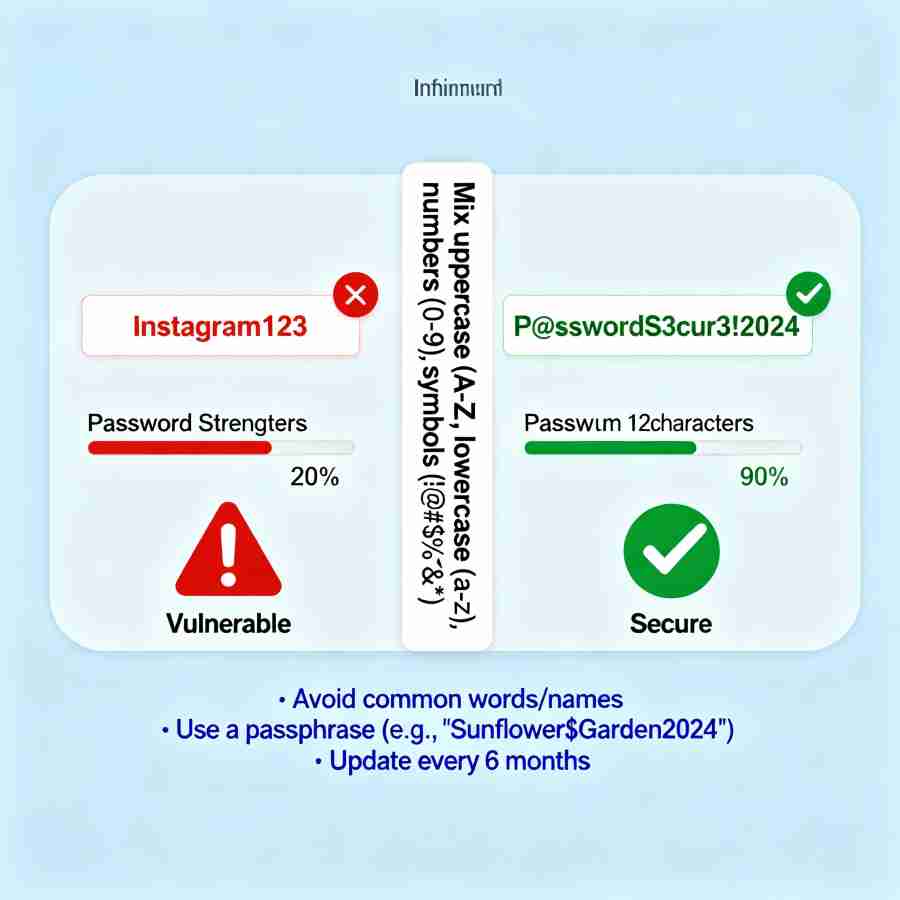
Strong, unique passwords are non-negotiable. Yet “123456” remains one of the most common passwords globally.
A strong password should be at least 12 characters, mixing uppercase and lowercase letters, numbers, and symbols. But length matters more than complexity. “MyDogSpotIs7YearsOldAndLovesBeachBalls” is stronger than “P@ssw0rd!” because it’s longer.
The solution? Password managers like 1Password, LastPass, or Bitwarden generate complex passwords, store them securely, and automatically fill them in. You remember one master password; the manager handles everything else.
Change passwords regularly—at minimum every six months. If you hear about a data breach at any service you use, change that password immediately.
Two-Factor Authentication: Your Security Lifeline
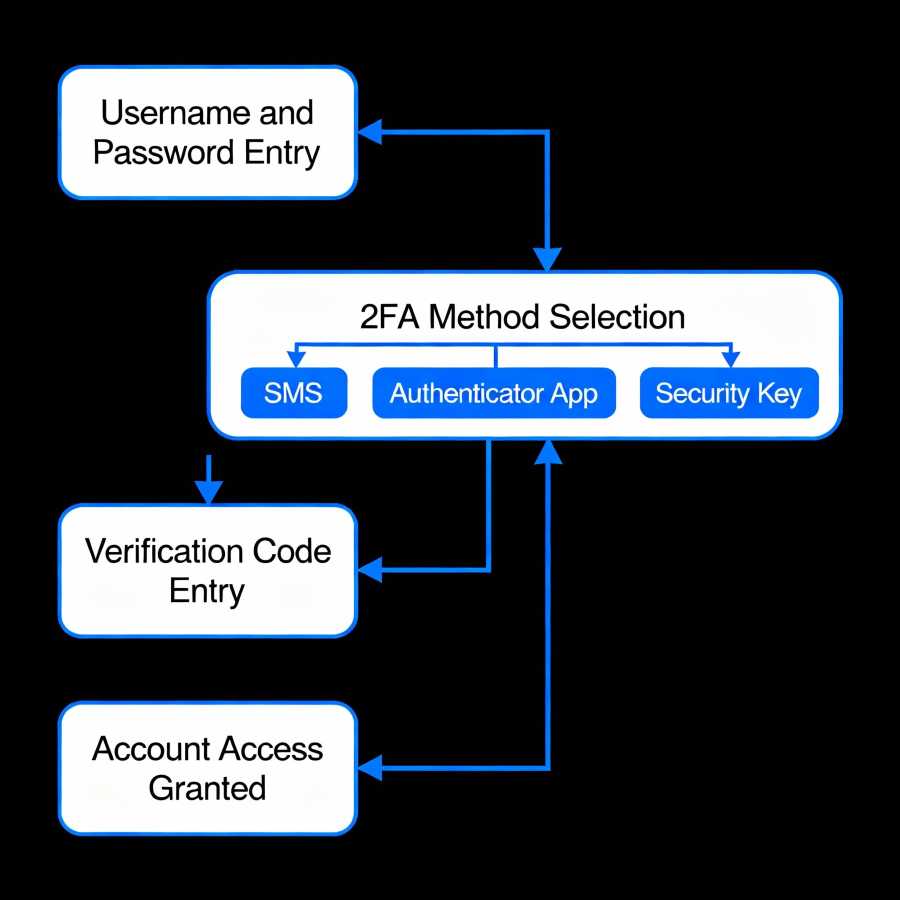
Two-factor authentication (2FA) makes your accounts exponentially more secure. Even if someone steals your password, they can’t access your account without a second verification step.
Not all 2FA methods are equal. SMS-based authentication is vulnerable to SIM swapping. Authentication apps like Google Authenticator or Authy are much more secure. The strongest option? Physical security keys like YubiKey—these require physical presence to log in.
Enable 2FA on every platform that supports it. The minor inconvenience of an extra login step is worth the massive security boost.
Recognizing and Avoiding Phishing Attempts
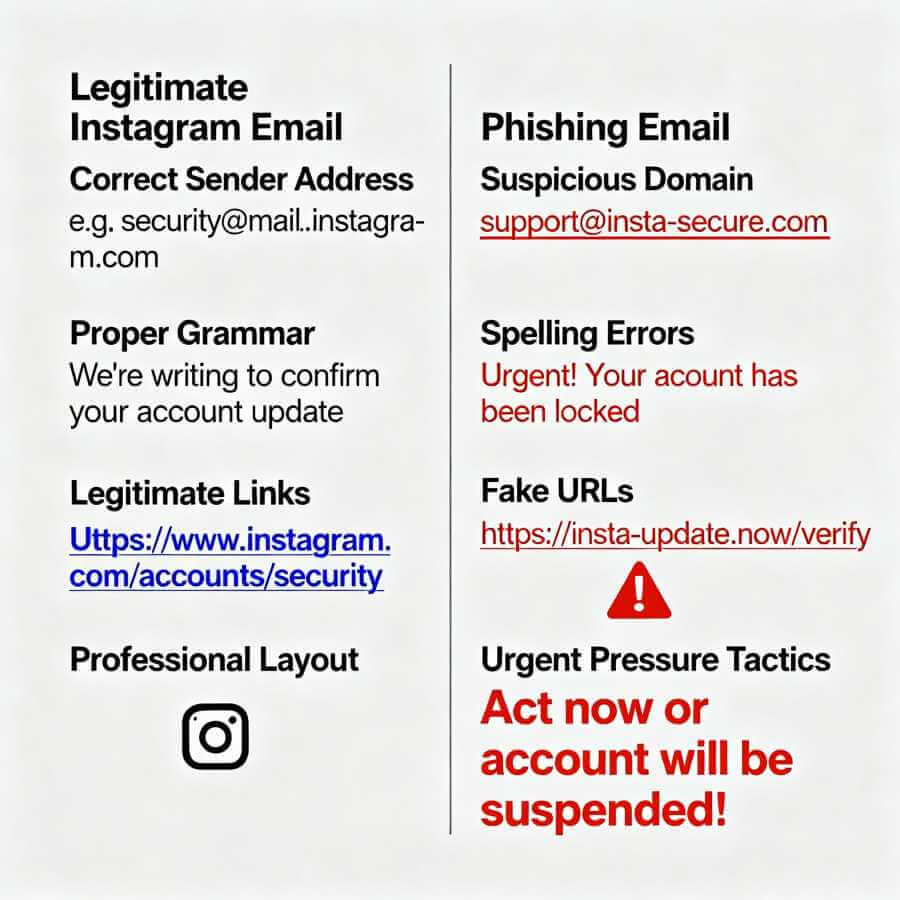
Phishing attacks have become incredibly sophisticated. Gone are the days of obvious scam emails with terrible grammar. Modern phishing attempts look legitimate, use correct branding, and create convincing scenarios.
Learn to spot the red flags: Legitimate companies never ask for your password via email or DM. They won’t threaten to delete your account unless you “verify” immediately. They don’t create artificial urgency or pressure you to act without thinking.
Always verify requests independently. If you receive an email claiming to be from Instagram, don’t click the link. Instead, open Instagram directly (type the URL yourself or use your bookmarked link) and check your notifications there. If the message was legitimate, you’ll see it reflected in your official account.
Examine URLs carefully. Phishers create domains that look almost identical to legitimate ones: “lnstagram.com” instead of “instagram.com” (notice the lowercase L instead of uppercase I). These subtle differences are easy to miss when you’re rushing.
Be especially wary of verification requests, prize notifications, or partnership opportunities that arrive unsolicited. When something seems too good to be true or creates unnecessary pressure, pause. Verify through official channels before taking any action.
Third-Party App Audits
Most of us have connected dozens of apps to our social media accounts over the years. Scheduling tools, analytics platforms, contest entry forms—each one maintains some level of access to your account data.
Conduct regular audits. Go through your connected apps and remove anything you’re not actively using. On Instagram, find this under Settings > Security > Apps and Websites. Facebook has similar settings under Security and Login. Twitter, LinkedIn, and other platforms offer comparable options.
Ask yourself: Do I still use this app? Do I trust this company with my account access? What permissions does this app have? If you can’t confidently answer these questions or the app hasn’t been updated in years, remove it.
When connecting new apps, review the permissions carefully. Does a follower counter really need permission to post on your behalf? Probably not. Grant the minimum access necessary for the app to function. This limits potential damage if the service gets compromised.
Research apps before connecting them. Look for reviews, check how long the company has been operating, verify they have proper security measures in place. Unknown apps requesting extensive permissions should raise immediate red flags. When building your social media presence, work with established, reputable services that prioritize security.
Account Recovery Preparation
Hope for the best, prepare for the worst. Having a recovery plan before you need one makes a huge difference if your account gets compromised.
Save backup codes when platforms offer them. Most social media sites provide backup codes when you set up 2FA—download these, print them, and store them somewhere secure. They’re your lifeline if you lose access to your authentication method.
Keep detailed documentation. Record your account creation date, original email address, and any identifying information platforms might request during recovery. This sounds tedious, but it dramatically speeds up account recovery processes.
Link a recovery email that you actively monitor. Make sure this email is itself secured with a strong password and 2FA. Your recovery email is only useful if you can actually access it when needed.
Take screenshots of your account periodically. If you need to prove account ownership to a platform’s support team, screenshots showing your dashboard, analytics, or settings can serve as verification evidence.
Connect your accounts to multiple verification methods when possible. Having backup phone numbers or additional email addresses linked to your account provides alternative recovery routes if your primary method fails.
The Business Account Consideration
Business accounts face additional security challenges because they’re more valuable targets. They have more followers, more data, and more at stake.
Never share login credentials with team members by giving them your password. Most platforms offer collaboration features that grant specific permissions without sharing full account access. Instagram allows you to add partners and employees with defined roles. Facebook Business Manager provides granular permission controls. Use these features.
If team members need account access, create separate logins with appropriate permission levels. When someone leaves your team, you can remove their access without changing your main password. This is basic security hygiene that many small businesses ignore until they face consequences.
Implement company-wide security policies. Require team members with account access to use password managers, enable 2FA, and follow security best practices. Your security is only as strong as your weakest link.
Consider cyber insurance for valuable accounts. If your business depends heavily on social media, insurance that covers account compromise, data breaches, and related losses provides important protection. Policies vary widely, so review coverage carefully.
Monitor account activity regularly. Most platforms show recent login locations and devices. Check these periodically. If you see logins from locations you don’t recognize, change your password immediately and review your security settings.
Read More: What happens to your social media when you die?
Mobile Security Matters
Most social media access happens on mobile devices. Enable biometric security on your device. Be cautious about public Wi-Fi—use a VPN if necessary. Keep your OS and apps updated. Download apps only from official stores. Review app permissions and revoke unnecessary access.
Monitoring Your Digital Footprint
Set up Google Alerts for your brand name. Regularly search for fake profiles impersonating you. Monitor your credit if you’re a public figure. Check emails for security notifications. Use “Have I Been Pwned” to check if your data appears in known breaches.
What to Do When Things Go Wrong
Despite best efforts, breaches happen. Knowing how to respond quickly minimizes damage.
If you notice unauthorized access, act immediately. Change your password from a secure device. Enable or update 2FA if it isn’t already active. Check connected apps and remove anything suspicious.
Document everything. Take screenshots of unauthorized posts, changed settings, or suspicious messages. This evidence helps when reporting to the platform and proves to your audience that your account was compromised.
Report the breach to the platform immediately. Every major social media site has specific procedures for reporting compromised accounts. Follow these exactly—proper reporting often determines how quickly you regain access.
Notify your audience as soon as possible. Post from alternative accounts or platforms explaining the situation. This prevents your followers from falling for scams posted from your compromised account and maintains trust by showing transparency.
Review what happened and learn from it. How did the breach occur? What security measures were missing? Implement stronger protections before resuming normal activity. A breach is traumatic but also educational if you use it to improve your security posture.
The Privacy Settings You’re Probably Ignoring
Each social platform offers privacy settings most users never explore. These settings provide important control over your data and account security.
Review who can see your posts, contact you, or find your account through search. Not everything needs to be public. Balance visibility goals with security needs based on your specific situation.
Limit data collection where possible. Platforms track tremendous amounts of user data. While you can’t eliminate tracking entirely, privacy settings often let you reduce it. Turn off ad personalization, limit data sharing with third parties, and restrict how your information appears in search results.
Control tagging and mentions. Don’t let anyone tag you in posts without approval. This prevents association with content you haven’t vetted and reduces exposure to phishing attempts that use tags to gain credibility.
Disable location services unless absolutely necessary. Broadcasting your real-time location creates security risks, especially for high-profile accounts or business owners. If you do share locations, do so after leaving rather than while still present.
Regularly review and update privacy settings. Platforms change settings and add new features constantly. What was private last year might be public now. Schedule quarterly privacy audits to ensure settings remain as you want them.
Read More: Will Instagram and Facebook leave EU?
Balancing Security and Growth
Growing your presence requires openness. Locking everything down defeats the purpose. Finding balance is key.
Be strategically visible—share enough to connect authentically while protecting sensitive personal information. Engage carefully with new contacts, verifying legitimacy before sharing information or clicking links.
Use separate accounts for personal and business when possible. Consider professional social media growth services that prioritize security. Legitimate services use secure methods and never request your password.
Test security regularly without paranoia. Check settings monthly, update passwords quarterly, review connected apps biannually.
Creating a Security Culture
If you manage accounts for a business, establishing security culture prevents most breaches. Train everyone with account access on best practices. Make security part of onboarding. Encourage reporting without punishment—fear causes people to hide mistakes. Lead by example in demonstrating good security practices.
Read More: How to download Instagram Videos in HD
Social Media Security – FAQ
Q1: What is the most common way social media accounts get hacked?
A: Phishing attacks remain the #1 way accounts get compromised. Hackers send convincing DMs or emails impersonating legitimate platforms, asking you to “verify” your account by clicking a link and entering your password. The links often look nearly identical to real platforms (like “lnstagram.com” instead of “instagram.com”). To protect yourself, never click links in unsolicited messages. Instead, open the platform directly through your bookmarks or by typing the URL yourself, then check if there’s actually a message waiting in your official notifications.
Q2: Is two-factor authentication (2FA) really necessary?
A: Yes, absolutely. 2FA makes your accounts exponentially more secure—even if someone steals your password, they can’t access your account without the second verification step. However, not all 2FA methods are equal. SMS authentication is vulnerable to SIM swapping (where hackers impersonate you to your carrier and steal your phone number). The best options are authentication apps like Google Authenticator or Authy, or physical security keys like YubiKey. The minor inconvenience of an extra login step is worth the massive security boost.
Q3: How often should I change my social media passwords?
A: Change your password at minimum every six months. However, if you hear about a data breach at any service you use, change that password immediately on all platforms. A strong password should be at least 12 characters long and mix uppercase and lowercase letters, numbers, and symbols. Better yet, use a password manager like 1Password, LastPass, or Bitwarden to generate and store complex passwords—you only need to remember your master password.
Q4: What should I do if my account gets hacked?
A: Act immediately. Change your password from a secure device, enable or update 2FA, and check all connected apps to remove anything suspicious. Document everything by taking screenshots of unauthorized posts or changed settings. Report the breach to the platform immediately using their official compromised account procedures. Notify your audience from alternative accounts to prevent them from falling for scams posted from your account. Finally, review what happened and implement stronger security measures before resuming activity.
Q5: What are third-party app security risks and how do I manage them?
A: Every app you connect to your social media accounts (scheduling tools, analytics platforms, etc.) maintains some level of access to your data. When these services get hacked, your accounts become vulnerable. Conduct regular audits: go through connected apps and remove anything you’re not actively using. Ask yourself: Do I still use this? Do I trust this company? What permissions does it have? When connecting new apps, review permissions carefully—grant only the minimum access necessary. Research apps before connecting them, and be suspicious of unknown apps requesting extensive permissions.
Bonus Tip: Keep backup codes when platforms offer them during 2FA setup. Download, print, and store them securely—they’re your lifeline if you lose access to your authentication method.
The Bottom Line of Social Media Security
Social media security isn’t optional. The platforms you use to build your brand and grow your business are valuable assets requiring protection.
Start with basics: strong passwords in a password manager, 2FA on every account, regular audits of connected apps and privacy settings, awareness of phishing attempts.
These steps take an hour to implement and minutes monthly to maintain. Compare that to weeks recovering from a breach and permanent damage to reputation that can never be fully recovered.
Protect what you build. Your future self will thank you.
Secure Your Social Media Presence
At GTR Socials, we understand that growing your social media presence and protecting it go hand in hand. We help businesses build authentic engagement while maintaining the security and integrity of their accounts.
Looking to grow your presence securely? Explore our trusted social media services designed with both growth and security in mind.
Learn more at gtrsocials.com about building a social media presence that’s both powerful and protected.
Security isn’t just about preventing disasters—it’s about having peace of mind to focus on what really matters: connecting with your audience and growing your brand.







