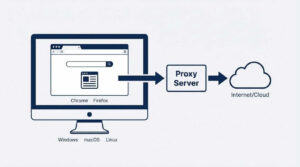
The digital backbone of every modern organization is undergoing radical transformation. As cyber threats evolve at unprecedented speeds and businesses demand faster, more reliable connectivity, the way companies approach IT infrastructure management has fundamentally shifted. For tech professionals, business leaders, and IT decision-makers, understanding these infrastructure trends isn’t just important—it’s essential for maintaining competitive advantage in 2025.
Table of Contents
The Evolution of IT Infrastructure: From Reactive to Proactive
Traditional IT infrastructure management operated on a reactive model: problems occurred, IT teams responded, and services were restored. This approach left organizations perpetually vulnerable to costly downtime, security breaches, and operational disruptions. Today’s IT infrastructure demands a fundamentally different approach.
Proactive IT infrastructure monitoring now leverages artificial intelligence and machine learning to predict failures before they occur. Instead of waiting for a server to crash or network bottleneck to cripple operations, modern IT infrastructure systems analyze patterns, anomalies, and historical data to identify potential issues days or weeks in advance. This represents a seismic shift in how organizations protect their digital assets and maintain operational continuity.

The convergence of automation, AI-powered analytics, and distributed computing has created what industry experts call “Intelligent IT Operations,” or AIOps. Rather than manual intervention, IT infrastructure now relies on intelligent systems that detect anomalies, predict failures, and implement remediation automatically. For organizations managing complex IT infrastructure across multiple locations and cloud environments, this automation proves indispensable.
Bringing IT Infrastructure Excellence to Local Communities
While IT infrastructure challenges are global, their impact is intensely local. Communities like Hilliard, Ohio—recognized as the Best Suburb To Do Business for two consecutive years—exemplify how local organizations leverage advanced IT infrastructure to compete in a digital economy. From high-tech startups to established manufacturing firms, healthcare providers, and financial institutions, Hilliard’s diverse business ecosystem demonstrates that modern IT infrastructure management isn’t just an enterprise concern.
As the city hosts over 1,100 companies employing more than 17,000 people, the IT infrastructure decisions these organizations make directly impact their competitive positioning, customer service capabilities, and long-term sustainability. Whether through internal expertise or partnerships with specialized providers, Hilliard businesses that prioritize robust IT infrastructure strategies position themselves to lead in their respective industries while smaller organizations still relying on legacy approaches risk falling behind.
Hilliard businesses increasingly recognize that scalable enterprise cloud solutions represent the foundation upon which modern IT infrastructure success is built, enabling local organizations to compete effectively against larger regional and national competitors.
IT Infrastructure Challenges in 2025: What Every Tech Professional Should Know
The Cybersecurity Reality
Cybersecurity threats represent the most pressing IT infrastructure challenge facing organizations today. In 2025, cyber attacks have become more sophisticated, frequent, and costly than ever before. Organizations worldwide now recognize that traditional perimeter-based IT infrastructure security—firewalls and basic access controls—provides insufficient protection against advanced threat actors.
The emergence of AI-powered cyberattacks represents a particularly concerning development. Bad actors now deploy machine learning algorithms to identify vulnerabilities in IT infrastructure, craft sophisticated phishing emails tailored to specific users, and adapt attack strategies in real-time based on defensive responses. This arms race between attackers and defenders means IT infrastructure security requires constant vigilance and continuous updates.
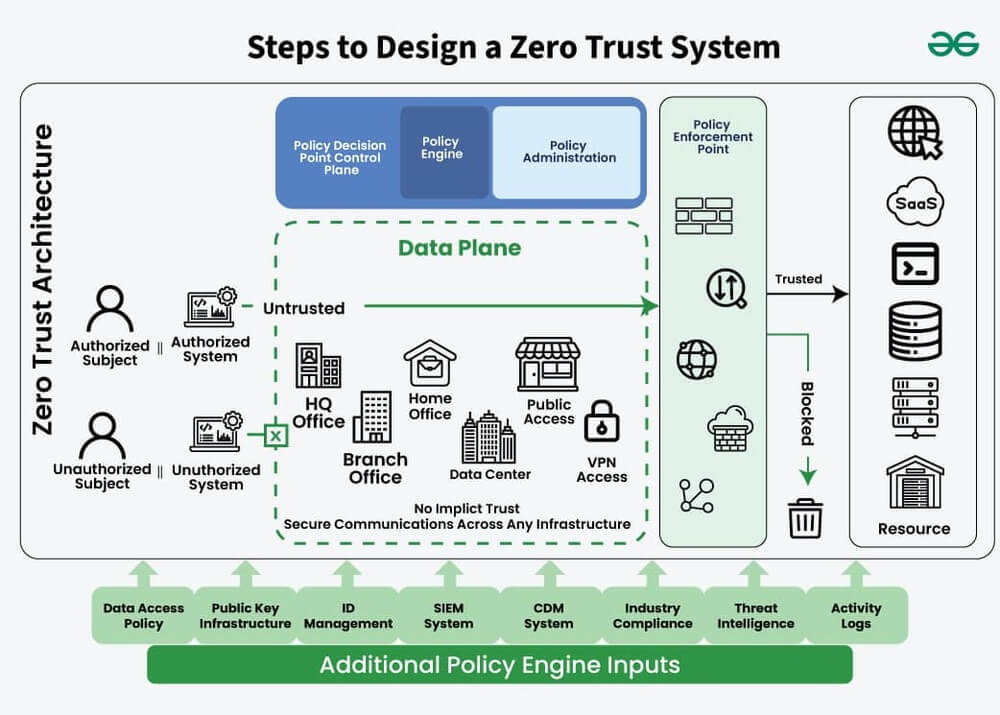
Zero Trust Architecture has emerged as the leading cybersecurity philosophy for IT infrastructure in 2025. Unlike traditional security models that trust users and devices once they’re inside the network perimeter, Zero Trust assumes all users and devices are potentially compromised. Every access request to IT infrastructure resources requires verification, regardless of user location or device history. This approach fundamentally restructures how organizations design and manage IT infrastructure security.
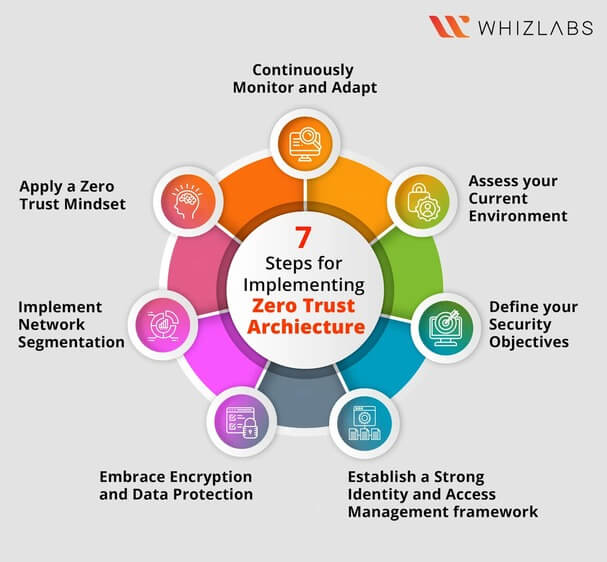
Network Latency and Performance Demands
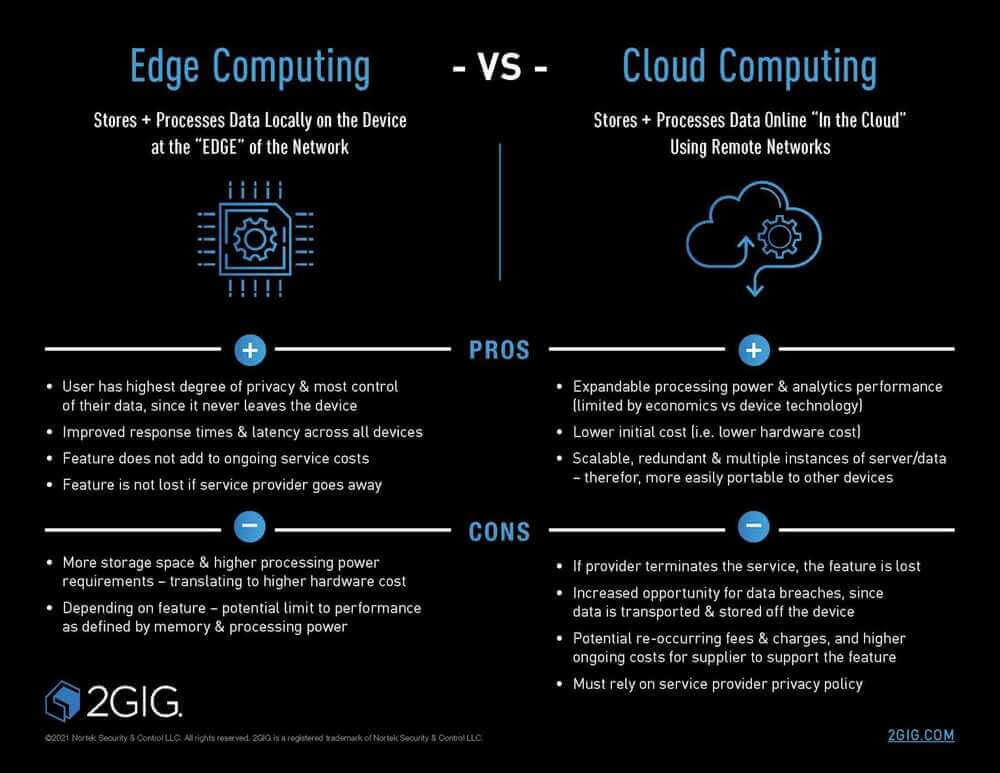
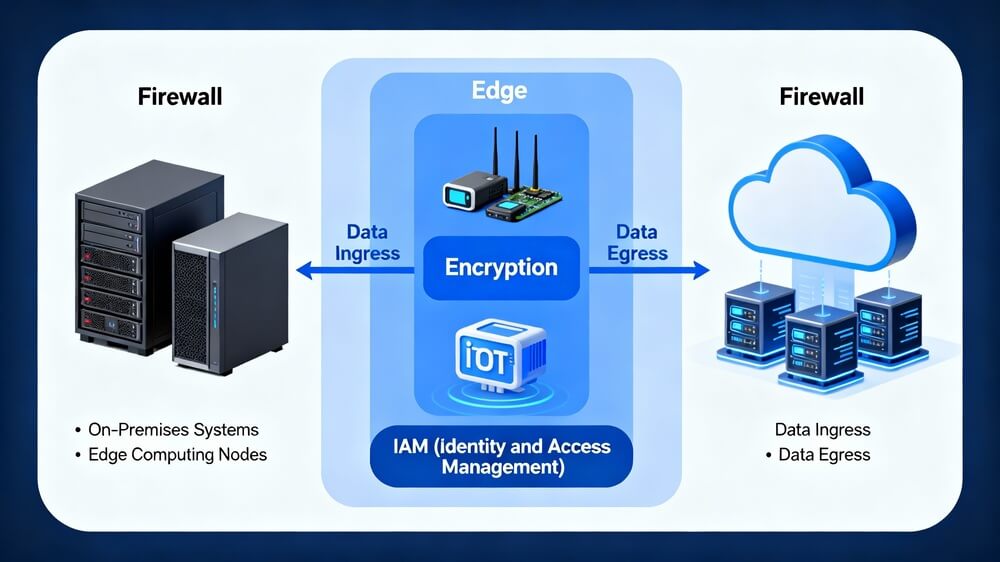
Modern applications simply cannot tolerate the latency inherent in traditional cloud-centric IT infrastructure models. Autonomous vehicles require millisecond-level response times from IT infrastructure systems. Telemedicine applications demand real-time processing. Industrial IoT sensors need immediate feedback for predictive maintenance. Traditional centralized IT infrastructure, where all data routes to distant cloud data centers for analysis, cannot meet these demands.
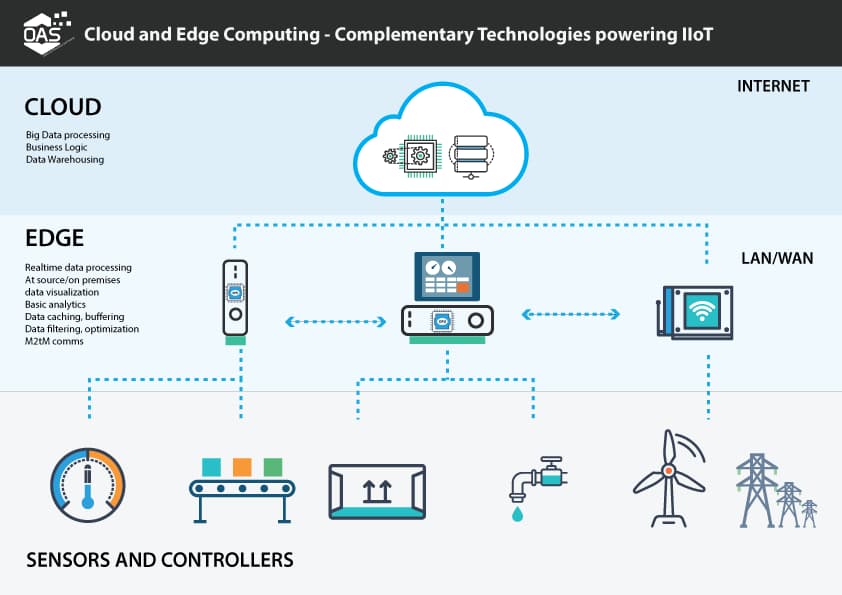
This recognition has sparked the rise of edge computing as a complementary architecture to cloud-based IT infrastructure. Rather than treating edge and cloud as competing models, forward-thinking organizations now design hybrid IT infrastructure strategies that leverage both. Edge computing handles time-critical processing locally, reducing latency and bandwidth costs, while cloud-based IT infrastructure handles broader analytics, long-term storage, and orchestration.
The distinction proves critical for IT infrastructure planning: edge computing isn’t replacing cloud infrastructure; it’s enhancing it. A modern IT infrastructure strategy requires understanding when to process data locally at the edge and when to aggregate it in centralized cloud environments.
The Multi-Cloud IT Infrastructure Reality
Single-vendor IT infrastructure strategies have become increasingly risky. Organizations that rely exclusively on AWS, Azure, or Google Cloud face vendor lock-in risks, potential service disruptions, and reduced ability to negotiate favorable pricing. Meanwhile, data sovereignty regulations in different regions require companies to maintain IT infrastructure in specific geographic locations.
Multi-cloud IT infrastructure strategies have moved from novelty to necessity. Rather than betting their entire IT infrastructure on one provider, leading organizations now strategically distribute workloads across multiple cloud platforms. This approach enhances IT infrastructure resilience by reducing dependency on any single provider and allowing organizations to leverage best-in-class services from different vendors.
Implementing multi-cloud IT infrastructure requires sophisticated orchestration and management tools. Container technologies like Kubernetes have become essential for managing IT infrastructure across heterogeneous cloud environments, enabling organizations to deploy and manage applications consistently regardless of underlying cloud platform.
Advanced IT Infrastructure Technologies Reshaping 2025
Hybrid Cloud Architectures
The future of IT infrastructure isn’t purely public cloud or private cloud—it’s hybrid. Organizations increasingly recognize that different workloads require different IT infrastructure environments. Sensitive customer data might require private cloud IT infrastructure, legacy systems require on-premises IT infrastructure, and elastic batch processing demands public cloud IT infrastructure resources.
Modern IT infrastructure solutions like AWS Outposts, Azure Stack, and Google Anthos enable organizations to build seamless hybrid IT infrastructure environments. These technologies extend cloud capabilities to on-premises data centers, creating unified IT infrastructure management experiences regardless of physical location.
AI-powered IT infrastructure orchestration platforms now automatically decide where workloads should run based on performance requirements, cost constraints, security policies, and resource availability. This represents the next evolution in IT infrastructure management—intelligent systems making infrastructure decisions rather than human administrators.
Edge AI and Intelligent Processing
The convergence of edge computing with artificial intelligence creates Edge AI—machine learning models deployed directly on edge devices that process data locally without constant cloud connectivity. This proves transformative for IT infrastructure in applications from autonomous vehicles to industrial predictive maintenance.
Edge AI fundamentally changes how organizations architect IT infrastructure. Rather than sending raw sensor data to cloud systems for processing, organizations now deploy pre-trained models to edge devices. These devices make intelligent decisions locally, significantly reducing network bandwidth requirements and enabling real-time responsiveness impossible with cloud-centric IT infrastructure.
For IT infrastructure specialists, Edge AI represents both opportunity and complexity. Organizations must now manage model deployment, versioning, updates, and monitoring across thousands of distributed edge devices—a challenge that requires sophisticated IT infrastructure management tooling.
5G and Advanced Network Infrastructure
While earlier 5G deployments focused on bandwidth improvements, next-generation 5G implementations deliver transformative IT infrastructure capabilities. Stand-alone 5G (5G SA) and private 5G deployments enable organizations to build dedicated, controlled wireless IT infrastructure for critical applications.
Autonomous vehicles in manufacturing facilities, remote robotics operations, augmented reality training applications—these represent just the beginning of what advanced 5G IT infrastructure enables. For IT infrastructure professionals, understanding 5G deployment models, network slicing capabilities, and mobile edge computing integration has become essential expertise.
Implementing Robust IT Infrastructure Security Frameworks
Securing IT infrastructure in 2025 requires layered, comprehensive approaches. Single-solution security approaches prove inadequate against modern threats. Effective IT infrastructure security now encompasses:
Defense in Depth: Multiple security layers across IT infrastructure, from network perimeter protection to endpoint security to data encryption. If one layer fails, others provide protection.
Continuous Monitoring: Real-time visibility into IT infrastructure systems, user behavior, network traffic, and data flows. Security information and event management (SIEM) platforms aggregate data from across IT infrastructure, enabling detection of suspicious patterns.
Automated Threat Response: Intelligent systems that not only detect threats but automatically initiate response procedures, from isolating compromised systems to blocking malicious users, minimizing IT infrastructure damage.
Incident Response Planning: Documented procedures for responding to IT infrastructure security incidents, including clearly defined roles, communication protocols, and recovery procedures. Regular tabletop exercises and attack simulations ensure teams can execute these procedures effectively when actual incidents occur.
Employee Security Awareness: Human error remains the weakest link in IT infrastructure security. Comprehensive employee training, regular phishing simulations, and security culture development prove essential for effective IT infrastructure protection.
Disaster Recovery and Business Continuity in Modern IT Infrastructure
IT infrastructure failures don’t only threaten operations—they threaten organizational survival. A single day of downtime can cost millions for large enterprises, and small organizations may not survive extended IT infrastructure failures.
Modern IT infrastructure disaster recovery strategies emphasize cloud-based Disaster Recovery as a Service (DRaaS). Rather than maintaining expensive backup systems in physical data centers, organizations now replicate critical systems to cloud environments, enabling rapid recovery when disasters occur. This approach dramatically reduces disaster recovery costs while improving recovery capabilities.
Effective IT infrastructure disaster recovery requires:
Regular Backup Testing: IT infrastructure backups prove worthless if recovery procedures fail when actually needed. Organizations must regularly test IT infrastructure restoration procedures to identify gaps before actual disasters strike.
Clear Recovery Time Objectives (RTO): How quickly must critical IT infrastructure systems be restored after failures? Different systems demand different RTO targets, requiring prioritized recovery procedures.
Data Loss Tolerances (RPO): How much data loss can an organization tolerate? Answering this question determines backup frequency and replication strategy for IT infrastructure systems.
Geographic Distribution: IT infrastructure systems concentrated in single locations remain vulnerable to regional disasters. Effective IT infrastructure disaster recovery requires systems distributed across geographically diverse locations.
The Business Case: ROI of Modern IT Infrastructure Investment
Organizations investing in modern IT infrastructure management realize substantial returns across multiple dimensions. Reduced downtime directly increases revenue and productivity. Enhanced security prevents costly breaches. Proactive management extends hardware lifecycles, reducing capital replacement costs.
Research indicates organizations implementing modern IT infrastructure management strategies reduce overall technology-related costs by 20-30% while simultaneously improving service reliability and security posture. For every hour of prevented downtime, organizations save thousands to millions depending on organizational size and criticality of affected systems.
Conclusion: IT Infrastructure Management as Strategic Imperative
The IT infrastructure landscape of 2025 demands constant evolution and learning. Technologies that seemed cutting-edge just two years ago now appear dated. Organizations that fail to keep pace with IT infrastructure innovations risk competitive disadvantage, security exposure, and operational vulnerability.
For IT professionals, business leaders, and technology decision-makers, the message is clear: modern IT infrastructure management isn’t a cost center—it’s a competitive imperative. Whether through internal expertise development or partnerships with specialized providers, organizations must prioritize IT infrastructure investment, security, resilience, and continuous modernization.
As seen in the recent Apple executive shakeup, leaders have to be very careful about their plans and choices.
The future belongs to organizations that view IT infrastructure not as support for business but as business itself. In an increasingly digital world, the strength of IT infrastructure directly determines organizational success. Those who embrace this reality and invest accordingly will thrive. Those who don’t will struggle to compete.